Crypto hardware Plug-over attack
This article describes a vulnerability I found over two years ago in certain external USB and eSATA data carriers (hard drives, USB sticks) which use cryptography to help protect the data they carry. This vulnerability has been found during the evaluation of multiple data carriers of different manufacturers and it seems to be quite common. Since this vulnerability doesn’t seem device specific this paper has been written to be able to spread some knowledge and to warn the general public about it. All the manufacturers of the devices I tested which were vulnerable to this attack have been notified long ago. The vulnerability described in this paper has been named the ‘plug-over attack’.
The basics
Almost all of the protected data carriers out there use the following principle: The drive containing the protected data will not be available to the computer user as long as the right password (or fingerprint, keycode etc) is not supplied. After supplying the right authentication credentials to the unlock mechanism, the protected drive will become available to the user. If someone would find or steal the data carrier that person would need the same information to be able to get to the data, on which principle this entire protection scheme relies. This principle is shown in the schematic below.
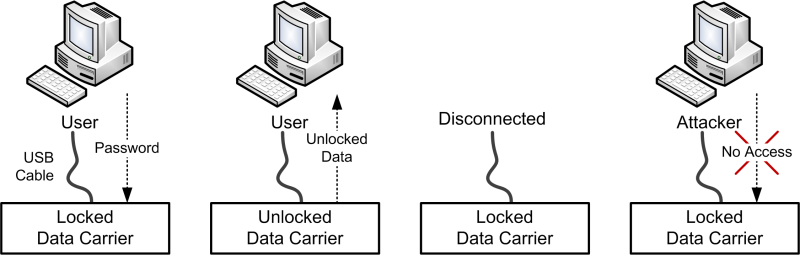
However, there seems to be a limitation to this protection which is not very far fetched but doesn’t seem to be well known to the general audience.
The Plug-over attack
After a user has supplied the right information to the cryptographic system protecting the data on the data carrier, the user is allowed access to the data. As soon as the data carrier gets disconnected from the system, the data carrier will be locked and protected again. Quickly plugging the data carrier into another system does not give access to the data due to the loss of power in the meantime. However, by keeping the data carrier powered during the transfer from one computer to another, it will not lock itself. Resulting in that the new system will have access to the data without supplying any form of authorization. Keeping the device powered during the transfer is in basics the ‘plug-over attack’. During the testing of this attack, it was found that there is generally no hurry in plugging the data carrier into another system, as long as the data carrier keeps being supplied with power the device will not lock. The exception to this are devices equipped with a timer which locks the device after a certain time of being idle.
How to keep the device powered
The question now is how to keep these devices powered during the transfer. This is easier than one would expect and there are multiple possibilities to do this. For USB devices which come with a USB Y-cable the easiest way is to connect one of the USB connectors to the new system and then to transfer the second connector as well. During the transfer the device will keep being powered by the new system. The steps of this attack are shown below.
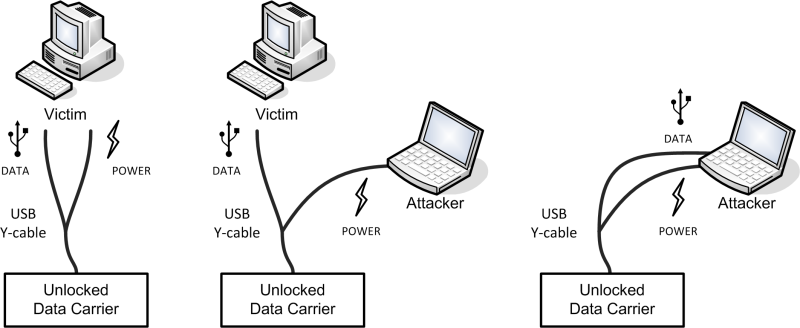
Many external USB hard drives come with the USB Y-cable included for systems which can not provide enough power for the hard drive to work. Even when such a cable is not supplied, an attacker might be able to switch the cable of a user to trick the user into unlocking the device on the next use and thus enabling the attack.
It should be noted that in theory it is not wise to connect the power sources of two systems together, which is done by connecting the cables to two different systems. However, during the testing of the attacks on several devices no issues were encountered.
Another approach will be to power the data carrier by other means; quite a number of data carriers contain a connector socket for an external adapter or USB power cable. Even when no adapter or cable is supplied with the unit, it still can have this connector. When powering the device through this socket, it will be possible to pull off the attack. If no such socket is available, a much more advanced way of performing this attack would be by opening the data carrier up and connecting a 5V power connector to the internal connections of the device. Performing the attack this way is not very likely and takes quite some effort, but it is possible to do it.
Yet another approach can be if the data carrier is connected through a ‘proxy’, for example a USB hub or an Express Card with eSATA or USB. If these proxy devices have a socket for external power the same approach as described above can be used. Some USB devices have these power connectors to be able to supply enough power to all the devices connected to them.
When these proxy devices have no socket for external power it is possible to power the devices by connecting a normal USB-to-USB cable. One end of the USB-to-USB cable will be connected to the proxy device in one of the normal USB sockets, the other end will be connected to a USB port on the target system. This way, instead of taking power from the USB port on the proxy, the USB cable will supply power to the entire proxy device. As soon as the proxy device gets disconnected from the victim machine it will stay powered and can be reconnected to the target machine. A schematic overview of this attack is shown below.
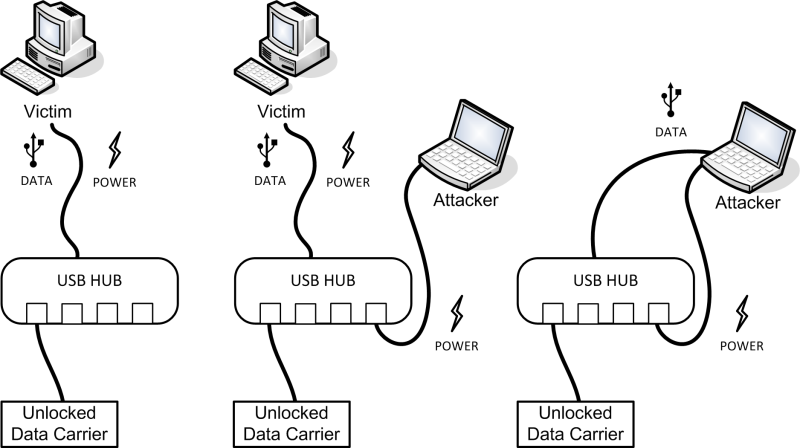
The above described attack has been successfully tested against USB hubs and USB Express Cards. Instead of connecting the data carrier to another system directly a variation of all the different attacks would be to use a mobile power source (like a battery) to power the data carrier during the theft. The data carrier can than be connected to another system at another location while being powered in the mean time by the battery. This can also be useful for acquiring unlocked data carriers of this kind during a forensic investigation.
How to solve this?
Besides knowing about this attack and not leaving your data carrier unlocked and unattended, a user can not do much about this attack. It might be that the manufacturers of the devices should come up with a solution. After contacting several manufacturers at least one manufacturer managed to solve this issue, this means that a solution should be possible for at least some of the devices. It might be possible to let the device recognize the disconnection from the system it is connected to or the switch to another system.
Some other approaches on how to prevent the likeliness of this attack would be to not to use a USB Y-cable to connect the data carrier and to not connect the device through a proxy like a USB hub or Express Card.
Conclusion
The vulnerability described in this paper does not break the encryption method of the mentioned data carriers, however it does attack a part of the implementation of it. Data carriers protected by cryptography are still protected against losing them, however, they are not fully protected against theft of the device. If an attacker has the ability to physically obtain the connected data carrier he might be able to steal it unlocked and can thus have access to the data on it.
Users should be aware of this vulnerability and should know that if they leave a device connected to their system, even if the system is locked, the data on the device might not be fully protected.
Update 26-06-2012
A couple of readers told me that the approach used in this article is similar to the approach that was used to perform a hot swap on the XBOX (the original, not the 360). With the XBOX it was possible to access the encrypted hard drive after booting the XBOX and hot swapping the IDE cable. While I actually performed this trick on quite some XBOX’s in the past myself I never made this connection. This XBOX trick however does show the danger of the weakness in certain hard disk crypto. More info on hotswapping the hard drive in the XBOX can be found here: http://forums.xbox-scene.com/index.php?showtopic=332179

Leave a Reply